Is Your Remote IT Team a Cover for Nation-State Hackers? The Urgent Need for IAL3 Verification
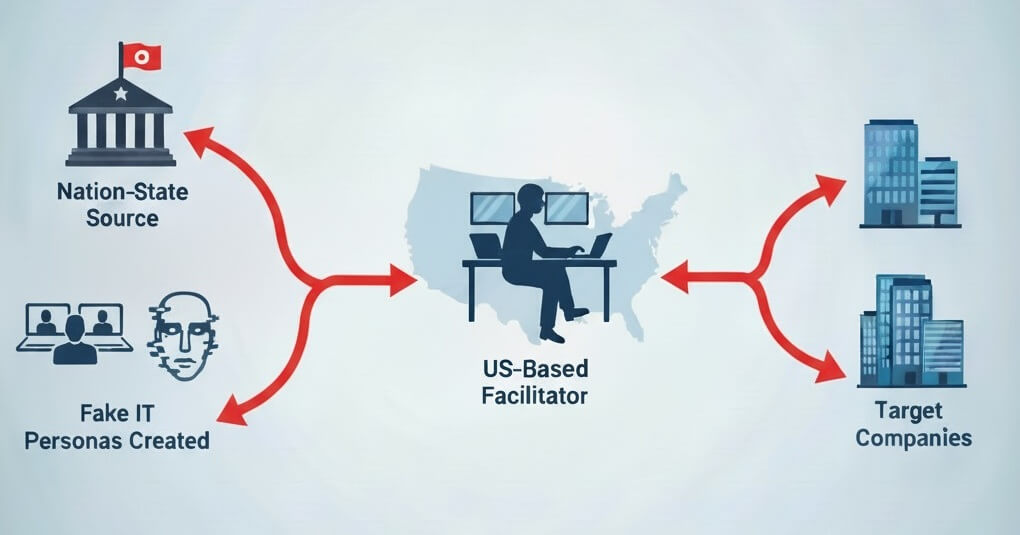
The remote work revolution brought flexibility, but it also opened a new front in cyber warfare. Sophisticated nation-state actors, including those from North Korea, are exploiting remote IT positions for espionage and financial gain. Your seemingly legitimate, high-performing remote employee—who aced the interview and consistently delivers—could be a hidden threat.
This isn't just a possibility; it's a documented reality, and traditional security measures are failing to stop it.
Why Traditional Vetting Fails Against Modern Threats
The old security playbook is obsolete. Nation-state operatives easily bypass standard checks that once felt secure:
VPN Detection: Defeated by residential proxies that make them appear local.
Video Interviews: Fooled by AI-powered deepfakes and real-time voice changers.
Behavioral Analysis: Masked by operatives trained to mimic cultural norms and work styles.
Background Checks: Circumvented using stolen or synthetic identities.
If your security strategy still relies on these methods, you have a critical vulnerability. Once inside, these actors operate as trusted employees, gaining access to your most sensitive systems, intellectual property, and financial accounts.
IAL3: The Unbeatable Defense Against Remote Infiltration
The new gold standard for remote security is Identity Assurance Level 3 (IAL3), a high-assurance verification framework defined by the National Institute of Standards and Technology (NIST).
In simple terms, IAL3 is a supervised identity proofing process that requires an individual to prove their identity in a live session with a trained agent, using their physical government-issued documents. It moves beyond digital checks to provide real-world, undeniable validation of who a person is and where they are located.
IAL3 in Action: Countering Top Nation-State Tactics
IAL3 isn't just another layer of software; it’s a direct countermeasure to the most advanced infiltration tactics used today.
It Defeats Deepfakes and AI Impersonation: The mandatory live, supervised session and biometric verification compare the real person against their official documents using trusted hardware. An AI-generated deepfake cannot pass this test.
It Exposes "Laptop Farm" Fraud: A common tactic involves a legitimate U.S. worker getting hired, only to ship their corporate laptop overseas to a nation-state operative. IAL3’s supervised physical presence and location checks immediately flag that the employee is not where they claim to be.
It Forces Bad Actors to Quit: Faced with an un-gameable identity verification process, most fraudulent actors won't even attempt it. They know IAL3 will expose them, so they often resign or disappear, silently solving the problem for you.
Tackling the "Rented Identity" Threat
Even the most complex fraud—where a legitimate U.S. citizen knowingly rents their identity to a foreign actor—is addressed by IAL3. By binding the initial, high-assurance identity verification to a physical authenticator (like a FIPS-certified YubiKey), you ensure the person who was verified is the same person logging in every day. This creates a continuous chain of trust that is nearly impossible for a proxy to maintain.
Secure Your Remote Workforce Today
A one-time background check at hiring is no longer enough. In an era of AI-driven threats, trust must be verified and adaptive. Implementing IAL3 isn't about employee monitoring; it's about workforce assurance—protecting your company, your data, and your legitimate employees from hidden threats.
Don't wait for a breach to reveal who is really inside your network.
Want a deeper dive into the strategies, ethics, and operational security of this approach? Read our complete guide here.
Ready to secure your remote operations and validate your workforce? Contact Trust Swiftly today to request a remote IT worker audit.