How It Works
Have a transaction or person that might be risky?
Notify them with an embedded form, E-mail, SMS or a hosted link to complete a self-verification.
Notification
User informed of review and directed to Trust Swiftly to complete verification.
Self-Verify
The user provides identity verification or completes dynamic requirements according to any risk scoring.
Authentication
Identity data is securely transferred to the business for confirmation and automated processing.
Dynamic Verification Paths
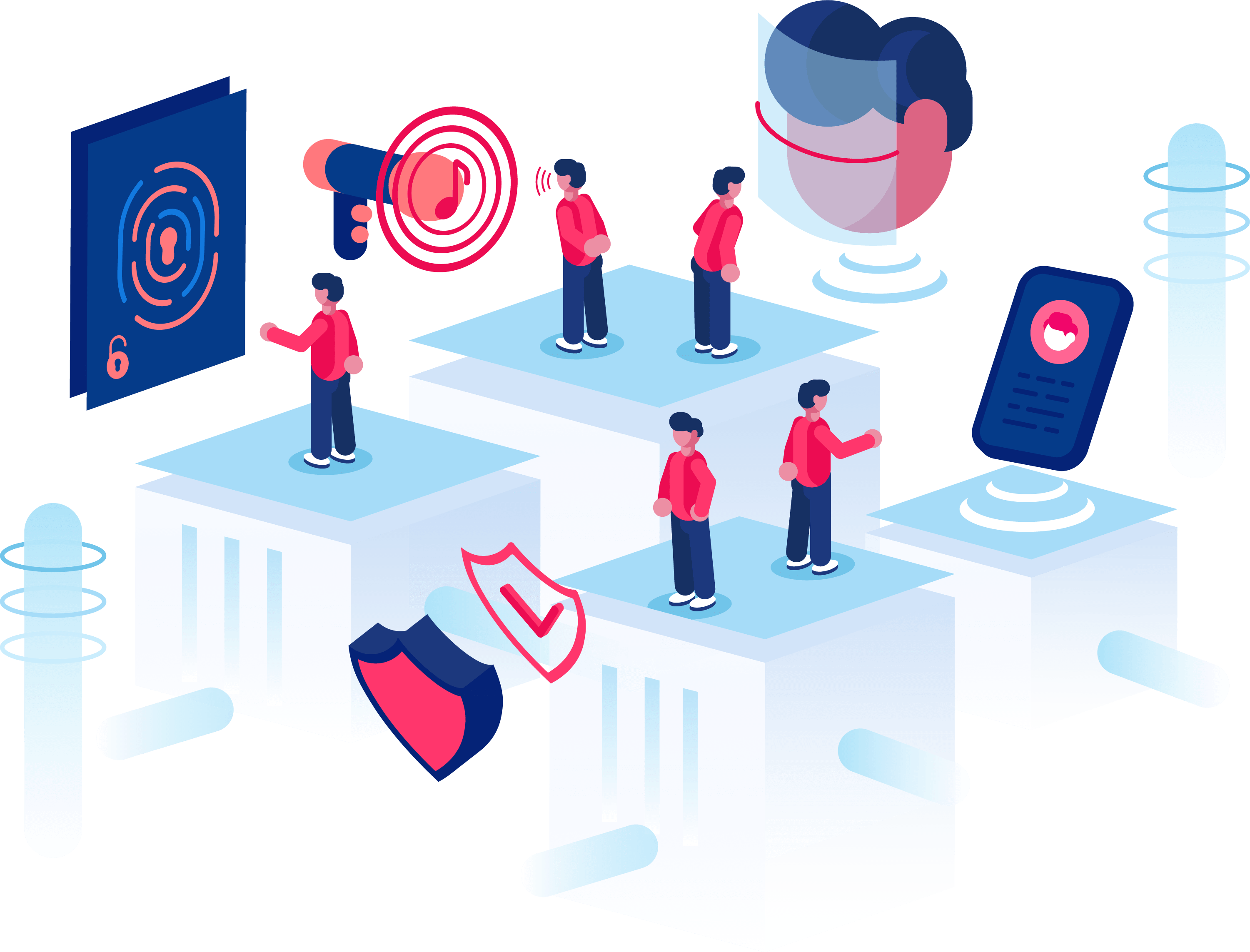
Verification Methods
Secure global identity verification that scales with zero overhead.
Trust Swiftly provides a central and dynamic platform to verify your users no matter your size or attacks faced.
- Rapidly respond to threats with dynamic verification
- Uncover existing fraud and identify patterns of bad users
- Global coverage allowing for growth without security compromises
- Compliance with privacy regulations using cost-effective solutions

Stop fraud before it becomes a problem by only targeting the bad actors.
Dynamic friction is critical to staying ahead of your competition while keeping fraudsters at bay. Identify bad users quickly by requiring additional verification. Putting good users in the fast lane and higher risks in further checks will create an environment that is safe for everyone. Synthetic identities, friendly fraud, chargebacks, and more all become things of the past with Trust Swiftly.










