The Definitive Guide to Finding Remote Nation-State Actors in Your Company
The New Frontline: A Hidden Risk in Your Remote Workforce
Remote work remains an excellent job option, but there are underlying risks. It has continued to expand, but some companies are recently advocating for a return to work, partially for cybersecurity precautions. Nation-states such as North Korea have taken particular advantage of remote IT positions for financial and informational gain.
Fundamental analysis no longer works; VPN detection (which residential proxies outsmart), language, behaviors, interviews, and even in-person recruiting processes can all be fooled. A new frontier solution for detecting nation-state actors is through supervised remote identity proofing and above-level verifications. Before we dive into Trust Swiftly’s solution, companies need to understand the operations of potential threat actors.
Beyond the Hype: Understanding the Modern Threat Actor
Not all these actors are super sophisticated, even though they have the word "nation" in them and are hyped up by the news and companies trying to sell services. It is also important not to fall for the red-scare approach and bring your inner McCarthyism, as finding nation-state actors is like a needle in a haystack and covers a wide spectrum when leveraging limited government resources. These IT workers can also come from unsuspecting countries; therefore, the scope should not be limited to North Korea.
Sophisticated ones will almost always have a backstory that allows them to avoid direct links to a particular country, such as claiming they were doing it for corporate or financial reasons only. The penalties for corporate espionage are much less as long as they don’t get tracked back to a specific nation. Plausible deniability is an essential skill that all nation-states understand and will follow for operational security. Many companies are more likely to be hit with corporate espionage than nation-state activity, but that is not publicized in the press, and companies like to keep it restricted for various reasons. These lines cross frequently, so it’s difficult to distinguish the origin of any malicious activity.
The Cat-and-Mouse Game of Government Detection
The government can’t unmask every worker at companies, as that would allow actors to better understand detection methods and become more sophisticated. For example, a simple early way to track some remote workers would be through biometrics and creating an AI model that detects outliers. Your face should appear in multiple independent places throughout a country to confirm presence and activity within the area you claim to be from. This, however, becomes a cat-and-mouse game where the integrity of feeds becomes paramount when using them as data sources.
To keep things simple, we will focus on the obvious fake IT workers. Companies should be prudent in their security posture to uncover low-hanging fruit and notify the proper authorities for the next steps of confirmed cases. Some of these actors shouldn't know they are discovered, as they could be confident in their persona, which allows them to fall for bigger traps and misinformation set up for them later in their careers. Compared to some countries, most Western nations take a more moral approach to handling these cases and use it for leverage on higher-priority issues.
Why Traditional Vetting Is No Longer Enough
There are tiers of nation-state actors, and the focus of this article will be on the middle echelons. The lower tiers can already be identified through technical means and screening controls. The upper tiers are more difficult to catch and require a bit of luck in combination with other factors to identify them. However, in all cases, they will likely be using a sophisticated array of tools and technologies that allowed them to be placed in your company.
Many companies won’t admit they have these workers and feel confident that they are blocking nation-states at the front door early during the recruiting process. Deepfakes, voice changers, fake or stolen backgrounds, professional interviewees, and more can be detected with some diligence nowadays without much work, which reassures businesses that they are proactively solving the problem. The problem is the unknown actors that made it through and are now operating as normal employees. They do their work well and have great feedback, ensuring access is maintained in your environment. Little do you know that they are a sleeper worker or simply collecting a big paycheck. Once they are in, they can also provide a detailed playbook for more of their external colleagues. The nuances of their mission can be vast, but that isn’t typically your company’s priority.
The New Standard: Using IAL3 to Unmask Hidden Threats
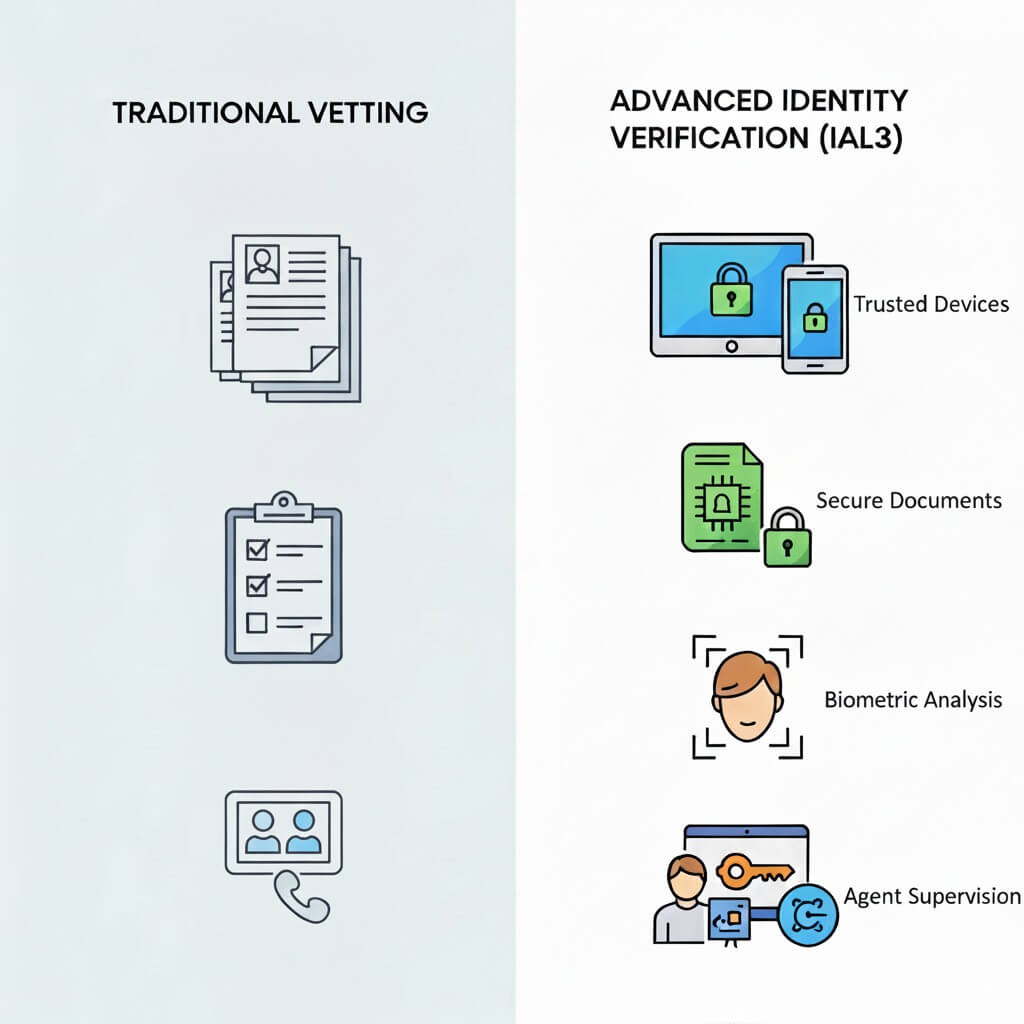
Businesses need to protect their bottom line and reputation, so employing these actors is a huge risk. A tangent analogy can be finding a ticking time bomb planted in your office. Don’t fret, though, as this is 100x less severe in consequences, and you are dealing with cyber warfare activity. The middle-tier actors can be tasked with information gathering and more benign financial gain activities. However, over time, these mid-tier actors can grow their operations with a bigger bank, as bribing people to commit illegal actions is a lot easier than coercing a proxy to commit an act of espionage. Depending on your industry, it will dramatically change any response you or the authorities will take.
NIST 800-63A-4: The Framework for Assurance
Understanding the background and motives of nation-states is critical, as the next step is identifying them. While there are many options, one that is simple, cost-effective, and works is Identity Assurance Level 3 (IAL3). NIST created 800-63A-4 guidance with many types of identity proofing options. The Level 3 assurance can be a benchmark to find nation-state actors, as this directive is being pushed across the US government as a requirement for companies to fulfill.
If you are not proofing employees at an IAL3 level, then you are missing a critical step in finding nation-state actors. The physical presence and supervised remote proofing session with a trained agent help identify these actors. While IAL3 is effective, it isn’t something you can likely roll out entirely to your workforce unless your budget allows for it. Instead, it should focus on the highest-value remote employees with the most privileged access to your IT environment or other sensitive positions.
How IAL3 Verification Exposes and Deters Malicious Actors
Through our years of experience finding bad actors online, we leveraged those skills to help find nation-state actors. Bad actors operate similarly, whether they are lone wolves, organized criminals, or nation-states; they all don’t like to do difficult work. They are taking shortcuts to achieve their goals through bad behavior.
Requiring completion of an IAL3 process using a tool like Trust Swiftly will cause many threat actors to quit their job or come up with another excuse as to why they can’t complete it. Nation-state actors don’t want to risk being caught, and they know IAL3 will expose them, unless they go through extreme measures which can lead to worse consequences, such as imprisonment. For example, a nation-state actor may have interviewed in person at your company three years ago, but since then flew back to somewhere in Asia and has been working comfortably remotely. They won’t risk coming back to the USA for a new IAL3 process in case, in the interim, they have been flagged by the government as a foreign agent.
Regular cleaning of the house (i.e., IAL3 recertifications) is required to be confident you are taking the proper measures to identify long-term plants. These IT workers with extended access are the highest-value assets a nation has, as they provide stability through financial and infrastructure means. There are few options to detect these actors that have gained the trust of your company when they outwit any technical or behavioral detections (such as techniques suggested by Google and Microsoft, which are mainly technical and pre-employment solutions).
With Trust Swiftly’s IAL3 solution, we require a physical presence check alongside identity proofing that validates their documentation throughout their term of employment at your company. If they are using a laptop farm, then IAL3 would immediately flag them, as the location verification will not pass. Unfortunately, your own IT assets and processes might not be secure enough to detect a nation-state IT worker. Mid-tier and above Nation-states have likely shifted away from laptop farms as they are easier to identify and use single proxy setups to avoid mass takedowns. Also, strategies published by the government or companies only work for an extended time before the actors adjust to remain undetected.
Instead, with Trust Swiftly, we manage the entire process end-to-end, providing companies a streamlined, superior verification process for remote workers. We can ship our verification kits directly to your employees, requiring minimal downtime in their day-to-day activities. During the quick verification session, we use trusted and secure hardware unconnected to your own IT to complete the verification process that identifies infiltrations, such as from a North Korean actor. Our verification kits and process operate externally from your entire IT environment, allowing for an independent audit of your employees with no technical integrations required. This siloed approach allows us to collect PII for a brief period, and then you own the data and future records of the proofed employee. In as little as a day, you can vet an employee and have multiple new data points that greatly increase your odds of detecting undercover IT workers.
The Ultimate Challenge: Detecting the Complicit or 'Rented' Insider
The one difficult tactic to detect remains rented, overemployed, or complicit IT worker fraud. In these cases, U.S. IT workers willingly allow a nation-state actor to use their identity in exchange for extra funds. They aren’t always informed they are dealing with a nation-state but ignore risks due to the financial gains, so they farm out some of their work. This comes at a risk for more parties, as facilitators are likely to be caught and charged with legal action. At the same time, whole networks of workers can be taken down in coordinated proceedings, as described by the Justice Department.
Career progression is another helpful sign for these advanced actors. Someone in a data center doing networking cabling doesn't typically jump to a senior software developer role. Most complicit facilitators will also not proceed with extensive verifications, as they don't want real recordings of their identity, which minimizes plausible deniability in the future. Nation-states also target people and look for specific profiles as facilitators in vulnerable positions, who are easier to manipulate, so if that person receives any extra verification request, it makes them second-guess everything, resulting in them coming clean even when they initially were complicit. The key is to work your way up the chain of command and go after the highest value insiders.
Most times, background analysis can show these activities where the person is employed at multiple positions or their finances do not correlate well to their proofed identity. Another method would be more frequent biometric verification checks requiring periodic identity and behavioral analysis to ensure they are the ones authenticating. Binding the IAL3 verification to a physical AAL3 authenticator (FIPS YubiKey) is key for streamlining this method of detection. Overall, these workers can be classified in the higher tier of threat actors and can usually be detected with vast intelligence data which companies typically don’t have access to, such as correlating all income sources and historical background analysis.
Implementing an IAL3 Campaign: A Guide to Operational Security (OpSec)
Before we dive into how to execute an IAL3 campaign to identify nation-state actors, there are some precautions that should be taken.
Employee Privacy: Employees may have privacy concerns, and IAL3 requires thorough vetting that might not be accepted. Education is key in the process, and framing the purpose will help employees understand it is a critical requirement to securely allow remote work.
False Positives: False positives are another extremely important factor to understand, as alleging a nation-state worker without full confirmation is a major risk. Governments might not confirm or deny if the person is a nation-state IT worker because the person is part of a broader investigation or for another reason.
Incident Response: If you attribute enough signals to a nation-state remote IT worker, how do you react and determine the response to the security event?
When you are ready to implement IAL3 verifications, it becomes a unique proposition for each business. The fewer people that are informed about the nation-state activity scanning, the better, as insider threats might already have vast reconnaissance on any communication throughout your entire corporate environment. Trust Swiftly should be treated similarly to an external pentest, with minimal knowledge about the purpose of the verifications.
For true operational security, we do not need to know if employees are a higher concern or if you even believe you have nation-state actors. We can provide our 3rd party analysis, and your internal team handles everything else if an anomaly is identified. For sophisticated insiders, we suggest zero acknowledgment of the issue and its true purpose. In this case, threat actors have no idea what triggered the IAL3 process and believe it may be directed by an audit or another department, such as HR, as a regulatory or security requirement. They should not know the reason is to uncover foreign actors but instead see the project as a normal compliance policy.
For these types of campaigns, vast groups of IT workers will all have to go through the verification process to not specifically target a suspect. The outliers will be identified or exposed throughout the campaign when they fail silently. Immediate action also might not be required, as you usually want to fully vet all employees before deciding how to react. Lastly, compartmentalization can be a useful strategy, when Trust Swiftly and internal teams are both initially separate from the insight and intelligence gathered, allowing fresh perspectives.
After Detection: How to Respond to a Nation-State Threat
What do you do once you believe you have uncovered a nation-state actor?
Microsoft provided good guidance, but we will provide some alternative ideas for special cases. They have a thorough, step-by-step set of actions that can be taken for remediating the issues. The cleanup process becomes extremely complex and is likely something that is handled case-by-case.
There are advanced techniques to increase the confidence score of an actor once suspected. One simple early method that used to work was political questions about a North Korean leader and analyzing their reaction. More subtle ways are now required for advanced actors, such as subliminal messages, images, information baiting, and video calls, where a professional can try to trigger specific cues over time to detect deviations. During most interactions, they have their own AI aiding in real-time to try to answer well, while the professionals require minimal guidance.
Another approach is to do nothing different by acting like everything is running normally. Not tipping off the threat actor is useful in case they also have contingencies in place. They could have an automated health check process on a system that only runs if that user is terminated, leaving a much bigger disaster to clean up. Some IT insider workers do not react well to being discovered and will do anything possible to damage or extort your business.
The ideal scenario is to uncover all the hidden threat actors in your company and do a coordinated clean sweep of them simultaneously to minimize any reactions from any single insider. Isolating each IT worker and understanding them will help you connect the wires across disparate teams and departments. In some cases, there will be no possible shared attributions or network analysis, which is the more difficult cleanup. Even if you get rid of them in one fell swoop, it doesn’t mean they won’t return in the future.
Adaptively changing your security measures will allow your company to always be one step ahead of new threat actors. Telegraphing these strategies is not something new to nation-states, and the key to continuously identifying them is using solutions that devise and hold better cards hidden under the table once the threat figures out how to bypass your traditional security measures.
Conclusion: Building Adaptive Trust for the Future of Work
In review, detecting nation-state actors becomes a manageable process when using Trust Swiftly in conjunction with your traditional insider threat tools and processes. Companies of all sizes should be doing their part to identify remote IT workers and deploy ready-to-use solutions that exist in the market. A failure to act will only allow a proliferation of nation-state strategies and resources that will eventually overwhelm backstop defenses such as the government. AI is making these actions especially important, with the level of detail becoming indistinguishable for enterprises to discover.
For companies looking to learn more about our supervised remote identity proofing process, contact us and request a remote IT worker audit today.