New Global Coverage for Identity Documents and Deepfake Prevention
We have updated our AI system to detect all identity documents with nearly every country supported and document type. The system is self-learning and constantly updated with support for any document your business collects. Even if there is a custom type of ID that another solution does not detect, we can create custom AI models for each customer to support their business. Supporting more countries and ID types securely allows businesses to expand to new regions. However, supporting multiple ID formats may bring in further fraud attacks as certain areas have increased fraud rates. Even if the best AI models are created to detect fakes, it is not enough as you are in a match-up of 1 AI vs 1 AI trying to win one game. Typically, in this scenario, we see the attacker win over the short-term, and it even seems to hold in the long-term. The problem with security is there is always an exploit, and covering every hole is almost impossible. The better approach is when you take multiple identity verification methods and create a holistic picture of an identity. When using a tool like Trust Swiftly, you can dynamically increase and decrease the security checks on the entire identity depending on the fraud detected. For example, when we believe a user is using a deepfake with a fake device, we can have them verify whether the device is rooted.
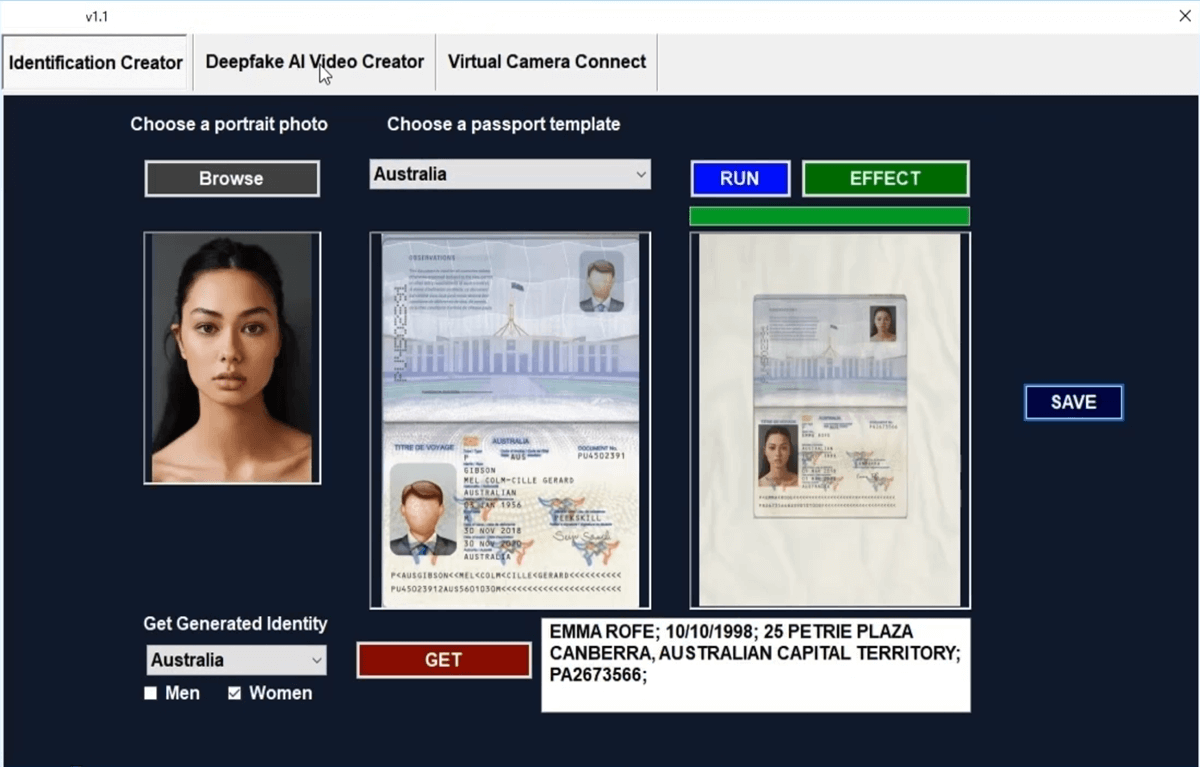
Supporting more countries and languages is insufficient in today’s identity verification environment. The fraudsters are advancing faster than ever with deepfakes that fool many systems. It is starting to reach the point where real IDs and liveness checks from people are almost indistinguishable from the fakes. As seen in the below videos and images, creating fake IDs and deepfakes is trivial. Also, nearly every single vendor is vulnerable to these attackers, with the bigger ones being targeted more since fraudsters can scale their business when they can exploit a more significant number of sites. One item from our research that we predicated is the injection of video and webcam streams using rooted devices or emulated devices. Many identity verification services rely upon unmodified feeds for capturing images but have little to no recourses against rooted device attacks. Checking for root and emulated devices is critical, even though some can obfuscate the root. Some AI models are being used to detect deepfakes in videos; however, one bypass method is to change the quality of the video to make it grainier / blurry. Some users have older phones, and unless a business wants to reject a significant subset, it is challenging to have stringent bandwidth and device requirements. Another way to detect deepfakes is to request random poses such as a thumbs up or bunny ears and then then pixels can be seen distorted during the movements. If the deepfake is pregenerated, it will fail, and the ones using real-time deepfakes without pixel perfection will be detected. Swift movements that result in distortions are ways to catch the less advanced methods. Another strategy is to access the front and back cameras to determine if the output is copied. Many deepfake solutions can't differentiate cameras, but it is a matter of time before they implement more advanced evasion methods. Finally, another method to defeat deepfakes is to require multiple faces into the stream, either them holding their ID or another person. A few deepfake software programs have difficulty identifying which face to swap if more than one face is detected. Monitoring all identity attributes will allow you to detect spikes due to a fraud attack. We still see manual oversight and review by a human as critical in finding novel attack methods.
.png)
Deepfake Software with custom profiles to bypass KYC tools
 Next, taking in more angles and images will further increase the detection of deepfakes. The problem with adding additional steps for users is it increases friction and abandonment. Being aware of the balance is still something businesses should consider when adding in more identity spoofing checks. Having a customer rotate their head and blink only stops the most prominent cases of fraud. Even doing high-security checks with live chats over Zoom, Facetime, etc. can be spoofed, similar to how ID.me does trusted referee checks on an identity. This type of fraud is currently being used on streaming platforms like Twitch but is already being repurposed to bypass KYC apps. IDs and Selfies are only the start of an identity verification platform, and companies need to keep innovating to stay ahead of new vulnerabilities.
Next, taking in more angles and images will further increase the detection of deepfakes. The problem with adding additional steps for users is it increases friction and abandonment. Being aware of the balance is still something businesses should consider when adding in more identity spoofing checks. Having a customer rotate their head and blink only stops the most prominent cases of fraud. Even doing high-security checks with live chats over Zoom, Facetime, etc. can be spoofed, similar to how ID.me does trusted referee checks on an identity. This type of fraud is currently being used on streaming platforms like Twitch but is already being repurposed to bypass KYC apps. IDs and Selfies are only the start of an identity verification platform, and companies need to keep innovating to stay ahead of new vulnerabilities.Video showing camera injection on real mobile device
Video showing bypass on verification systems