Fraud Attacks on AI SaaS Companies the coming waves of chargebacks
We recently encountered an uptick in the industry for chargebacks and fraud attacks. More consumers are interested in AI-related tools, which has created a market for cheaper subscription subscriptions. The bad actors are getting more advanced and collaborating extensively to widen their targets. SaaS fraud usually has been an afterthought, but now they figured out multiple schemes to extract value due to the lack of security. They even use SaaS tools to speed up their systems (https://neverinstall.com/ai and https://rdp.sh for generating new device profiles instead of traditional RDPs). We have seen even companies with subscriptions of a few dollars get targeted due to the scalability of this type of fraud. Many of these accounts are either resold or the signups are part of a fraudulent affiliate scheme. If you have a generous affiliate program, you may want to revisit it to determine if there is any new fraud. Uncovering the motives of these attacks leads to some financial gain against your company.
There was plenty of chatter on Twitter and other social forums.
- https://twitter.com/rameerez/status/1665680257788026880https://news.ycombinator.com/item?id=36197024
- https://twitter.com/threehourcoffee/status/1681863151103660033
Even the fraudsters use Twitter to spread the latest news. The tamper method using Burp Suite or Tamper Dev, which is described more below, was one of their methods that is patched. Going through the different communities, we found they hit many AI SaaS companies in May and June when there were few defenses.
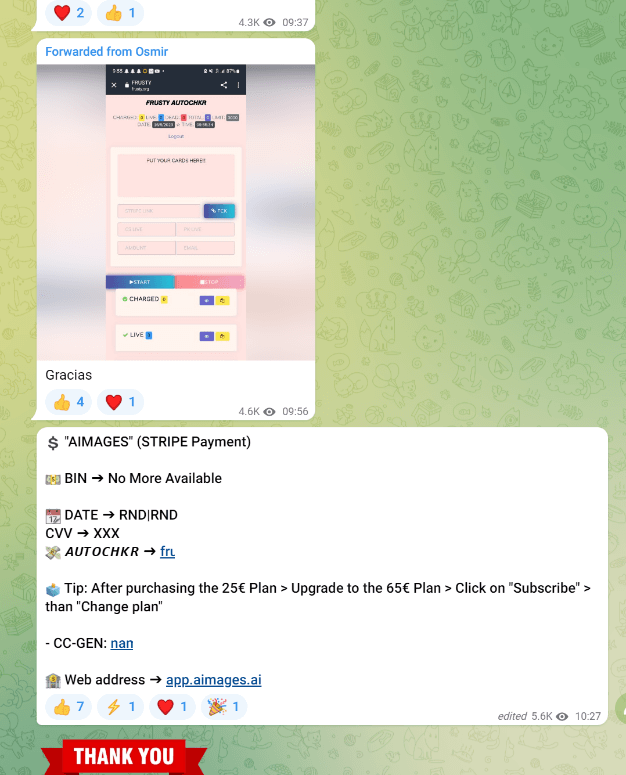
On the defending side, not one party should be put to blame as the entire system is highly complex, with multiple mitigating factors in place that failed. To start, there was a method for Stripe that resulted in people tampering with their requests and skipping some CVV checks or amounts charged, reverting to $1. This primarily affected low code integrations using checkout.stripe.com requests in the flow. Then specifically, they find certain sites that work with a specific BIN (first 6 digits of a cc) then there are tools to generate full card numbers using the bin as a starting point. They would then generate massive lists of cards to test amounts against hacked Stripe secret keys. Once they had cards that worked, they moved to their next phase. Then fraudsters were also sending requests to a fraud API that auto-modified Stripe checkout urls that would successfully be paid. We did not replicate the technical details, but from posts and videos by fraudsters, this appears to be the exploit they were using. We discovered users would send their checkout URLs to more advanced fraudsters, who would then complete the checkout process.
Fortunately, it appears the FBI is on the case as one of the auto checkout domains (Hyper Group) was seized by the government (Now the takedown notice is removed; There are other sites and bots built within Telegram, which will be more challenging to take down, but the fraudsters have moved to other platforms like Shopify). The updated versions seem more advanced, so simple rules like blocking the name “Jake Smith” (millions of blocked attempts came from this name) will not be sufficient. They are integrating rate-limiting bypasses, captcha solvers, proxies, and device profile changing, which makes detecting them more difficult. While many companies dislike adding friction, it might be a necessary protection if the fraudsters can improve their tools past the first lines of defense described above.
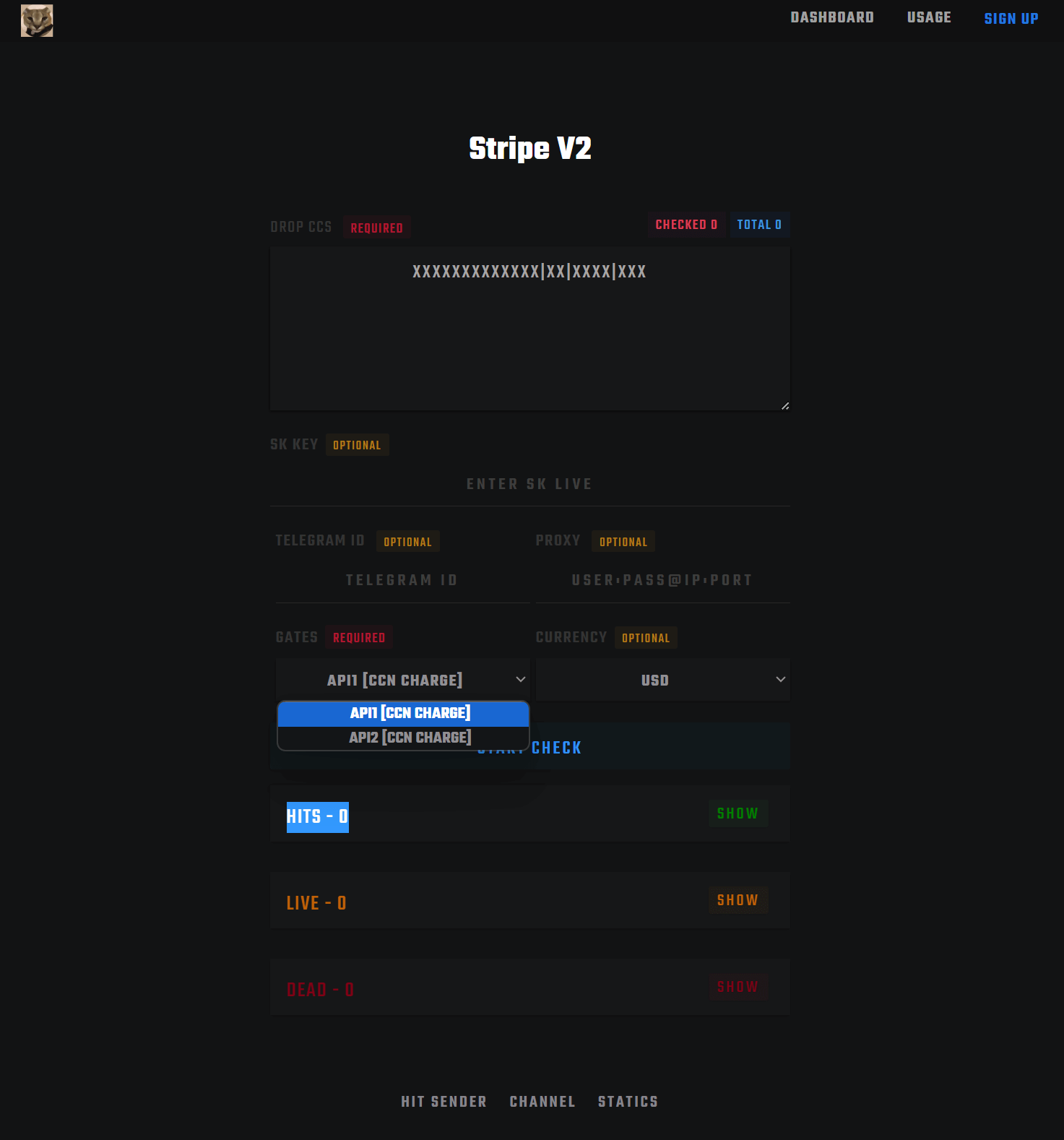
The manual methods for card tests might still work with fraudsters discussing the tampering and Burp Suite method using cheap labor from countries such as PH / VN. It is even easy enough to make these attempts on a phone, making the barrier to entry minimal. Overall, Stripe made some updates like a captcha and changes to their fraud detection, blocking the aggressive automated attacks. They even added some much-needed rule options (search for new) to stop repeated attacks based on counts, as some less advanced bots kept the same cards, IPs, and emails.
Then there is another tool called Mohio / Mohito for $30 that can automate even more of the bypass process. The video shows it in action.
Next, a script called SKBASED can automate many checks and allow the service to be sold. Fraudsters use stolen Stripe keys, and it appears even cracked keys, as there are discussions on cracking them to go through lists of card numbers to find ones that work. After some initial research, it seems that “cracking” means using a Python script to find Laravel sites with a vulnerability and obtaining their keys from the ENV file, which goes along with this news article. Once they have cards that work, they can get the AVS, Stripe risk score, and more for future valuable purchases. SaaS companies need to lock down their secret keys and ensure no leaks can cause abuse of their merchant account. Regular key rotation is another mitigation against any past leaks, too, as sometimes the hackers have a pool of keys they wait to use masquerading during a busy ordering season.
Also, now many of the fraud businesses know AI companies are easy targets when the setups ignore CVV. CVV is a critical check as many of the bulk cheap cards are missing that data making you a prime target for these cards. https://twitter.com/levelsio/status/1683200446222028804 We have seen a few clients remove CVV checks for low-risk scores, but having CVV requirements for higher-risk scores is critical. There are Telegram bots that help automate their attacks, and once they find a specific SaaS, they share it, which amplifies the fraud you may face.
Another item to watch for is these cards might be scraped from various sources. They are not always generated, and the fraudsters will move up the fraud chain when they have more funds. Either spend a few bucks for some cards or get them free from scrapers. The entire botting process can be automated with card numbers scraped and automatically sent to different SaaS providers to attempt charges. Even if you believe there is no affiliate scheme, it could be part of the testing or building history of the card using their emulated browser and IP to achieve future lower-risk scores.
Another scheme we have seen is users cashing out virtual and prepaid cards that were loaded with fraudulent funds. Some of these cards have no KYC, and the shoppers are looking for deals where they either overly dispute any payments or use your service as another layer of obfuscation of an illegal financing method. The card brands are adding better product identifiers for these non-reloadable prepaid/virtual cards. Sutton Bank / Monzo are examples of bins that typically result in higher fraud rates. Until these apps improve their KYC and fraud detection measures, you may need to set rules for high-risk bins if you see spikes in disputes.
Lastly, there are a few ideas online about preventing fraud. We suggest you consult with professionals before implementing system changes in case it causes an overreaction. For example, the EFW approach and refund are not a good idea, and hopefully, Stripe does not add this option (https://twitter.com/levelsio/status/1683532751767519239). There are several reasons why it should not be enacted. Sometimes it’s a mistake. Sometimes it doesn’t turn into a dispute. Sometimes the customer will regret their decision and cancel it if you notify them. Making a contact attempt is a critical step in managing early fraud warnings. Typically, you have a short window to resolve it before it turns into a dispute, so having this process automated will help optimize the number of revenue recoveries. If you want to optimize and automate your fraud prevention strategy, contact Trust Swiftly for an assessment today.