Fortifying Gaps in KYC Defenses
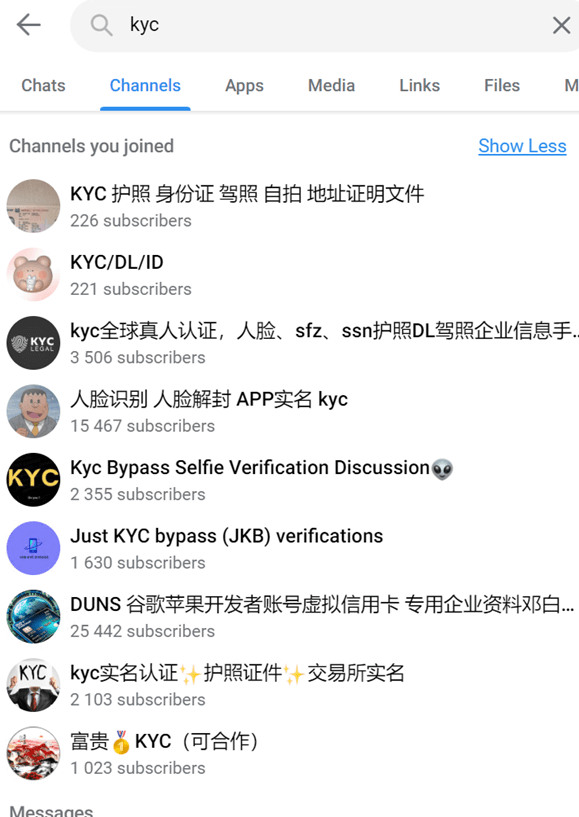
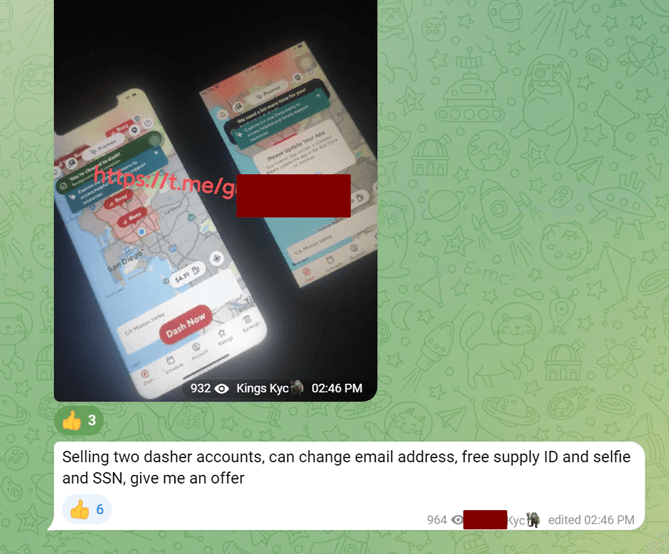
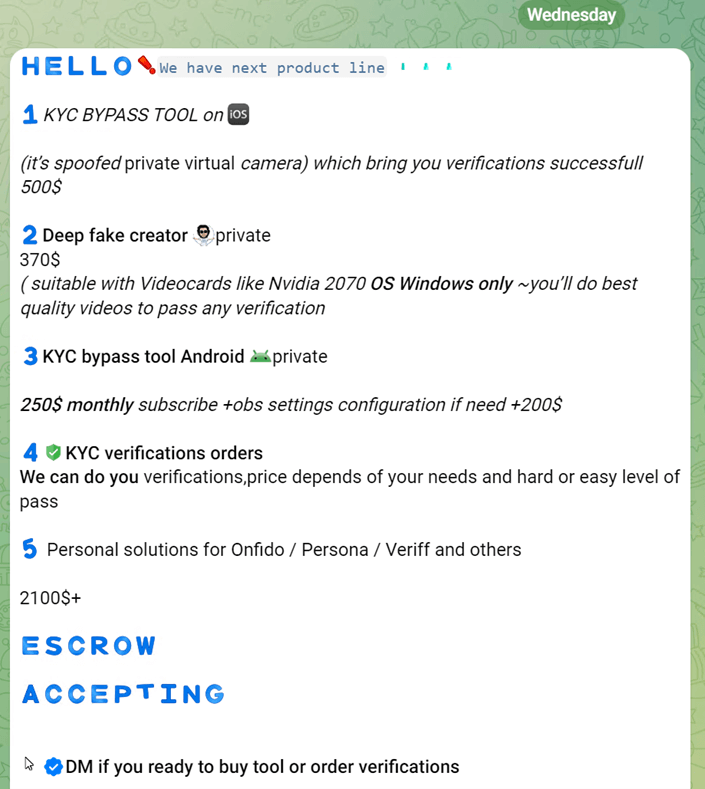
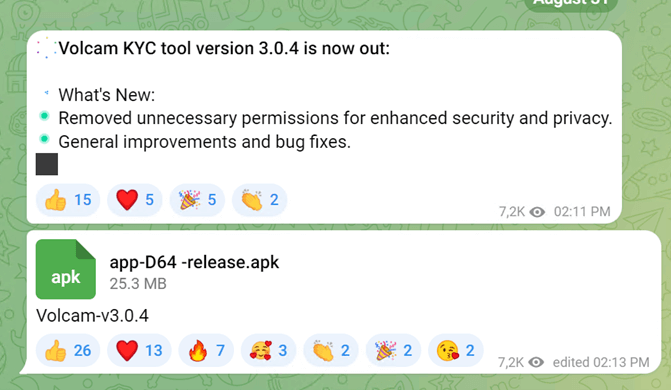
If anyone has been paying attention in the past few months, they will realize that most KYC protections have been breached at this point. The gates are wide open, and fraudsters encourage the peasants to pillage the castles. YouTube and other social media platforms are doing nothing or acting too late to slow down the training of fledgling fraudsters. While most guide videos (bypass KYC - YouTube and KYC Identity Verification | Facebook) are scams, some provide essential knowledge to bypass KYC systems. Taking a stroll through Telegram, there has been little slowdown in activity. The only thing the recent actions by Telegram and the authorities did was cause some groups to rename themselves to obscure signs and use further obfuscated language to escape any moderation. You can see in the screenshots from our research in a few communities that thousands work methodically to improve their fraud techniques each day.
While the gates might have been breached, there are still ways to restore the gaps in KYC. ID verification and selfie checks are the main ones being targeted now, so it is essential to have multiple methods to detect fake cases. Eventually, with many defenses, i.e., a wall against invaders, a dam against water, and a door against intruders, enough pressure will breach it. Trust Swiftly understood this issue 5 years ago when we added multiple verification methods. We had foresight that no verification would last forever, no matter how strong you make it. Eventually, gaps emerge, and a trickle makes it through, eroding the foundation. The fraud world has evolved tremendously over the years, and now, it has turned into a coordinated machine that uses the latest techniques and technologies to bypass different verifications. Whether it starts with social engineering or leverages deepfakes, there are ways around each KYC check.
Now, the remediation and cleanup of these bypasses takes time. Unfortunately, there is no silver bullet to verify an identity, and companies must use the best available tools. There are already solutions on the horizon, such as mDL and other cryptographically strong verifications that will thwart many attempts. NFC is another, but if you look at the first significant rollout and feedback from LinkedIn users, it points to a lot of frustration by end-users. However, now is when many companies need solutions and can not wait for mass adoption for more secure solutions. Working with a KYC provider who understands that and can create custom solutions is critical to strengthening your KYC posture.
The first bypass we will discuss is fake identity documents, with the US being the country analyzed. Driver licenses can only be verified accurately by the DMVs, who then use the AAMVA to propagate the service. However, the profitable non-profit AAMVA costs significantly for verifications and can quickly increase the cost per verification by a dollar. SMEs are also left out as they do not meet volume thresholds (10,000+ monthly), making the service not worth an investment. If you are investigating adding AAMVA (AAMVA-DLDV-Overview-for-Customers.pdf), it is a good measure but won’t do much for advanced fraudsters. They frequently discuss bypasses like using specific state IDs that don’t participate and using real information that another person socially engineered. Next, you may come across physical clone fakes, too, but for now, fraudsters are mainly resorting to digitally created IDs. A protection you can do now with little added cost is to require a live video streaming of an ID. Most AI videos and fakes are less than 5-10 seconds long. AI can only produce short clips and single images during this arms race lull. To counter it, you can set up a system that requests a longer video that combines audited randomness. For example, a user must show their front ID, flip it over, show the ID edges, auto turn the camera light on/off, put their finger on the top left corner, and do this for at least 15 seconds. You can use AI to guide and analyze the video to do an initial pass but still have a human review it for any other abnormalities. Not all will follow instructions to the tee, but having an exception process can keep those cases in line. No public AI fraud tools could mimic this behavior today, especially for digital IDs. The best they can do is to have a model swap out content in real-time by overlaying it to the image; however, doing enough random steps and difficult-to-reproduce sequences will show artifacts. Not every gap can be patched; the key is to focus on the main areas first to keep your overall defenses intact.
The next defense that needs to be fortified is selfie and liveness verifications. For these, doing longer videos is the best method available right now. Time is a good defense; even an ocean eventually dries up on a long enough timescale. Most users will rebel against this because of the added burden of effort required, but it should only be a stopgap until better solutions arrive. Usually, other verification methods, such as the ones used by Trust Swiftly, can spot abnormalities in an identity. AI fraud tools can now inject videos easily, but most are prerecorded looped clips. Combining a liveness check, i.e., moving in certain directions, with then a long 15-second video can identify most other deepfakes. The key to the defense is not to have to add manual human review but to create ways that AI can audit as a first-pass review. Supervised video sessions are definitely an option, but it gets ridiculous and time-wasting when a person tells someone to perform a bunch of actions to detect a deepfake. Creating an automated system is critical as it’s the simplest and most cost-effective solution.
Taking a bird’s eye view of your KYC fraud situation, you will likely come to similar conclusions outlined here, or at least you may face them in the next year. Every day, major enterprises and governments allow fraud to slip through, so no one has it solved, even if a vendor believes their tool is the best. A better defense is through an up-and-close experience where an identity can be reviewed with a personal touch. This takes time and investment, but the payoff can lead to a stable KYC program. Businesses should also be prepared to exit entirely from a specific verification, as there will be a point when the entire system requires a revamp. Having the flexibility and willingness to continue devising new ideas and iterations of a KYC program will leave a lasting impact. Biometrics and identity documents are still foundational elements, but as written above, tweaks like recording additional seconds can spot the gauntlet of fraud.
Research Images of Fraud KYC Communities