Bank and Wire Fraud Top Solutions to Prevent Losses
This post will delve into the underworld of banking fraud and some examples of wire fraud. The anatomy of the fraud ecosystem keeps getting more complex, with more bad actors joining and applying their skills across industries. Banks need to be especially aware of these fraud scams as they can instantly lead to 6- and 7-figure losses. Small, community and credit union banks are starting to be hit since they have lagged in investments with security and fraud prevention. The bad actors know this and have teams of researchers finding these easier targets. Understanding the multiple steps involved in fraud is required to create a better solution that prevents these scammers. Technology alone is not enough, and having well-trained back-office staff is critical. Policies and procedures that look out for new types of fraud are essential when evaluating your exposure to any wire fraud. A lapse in approval processes or checking the validity of a wire request will cause major headaches when you file a claim with insurance and deal with the legalities of the scam.
To start, we will follow the journey of typical bank fraudsters to see what they are doing and how they do it. There are a few entry points into bank fraud. One is spam services that send out phishing emails or texts to your customers, trying to have them log into their online banking account. Anyone who clicks these attempts puts them on the radar for follow-up targeting, especially for older people. They are trying to make a client click a link, and from there, anything can happen. The video below shows that these pages look highly professional and differ little from a bank's page besides the URL.
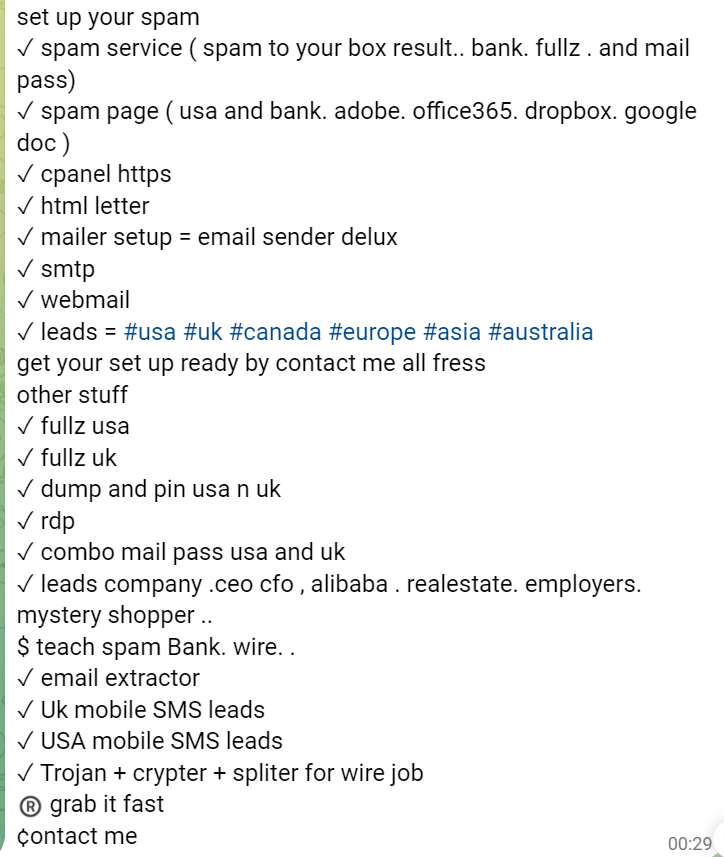 As seen above, a fraudster is advertising these typical services as a one-stop shop for bank fraud. A lot of technology goes behind these setups, and the more advanced ones have automated them to scale fake messages sent to thousands of people. They also utilize Email and SMS flooders, which will try to hide alerts and notifications about a wire. This is similar to the behavior we detailed about fraudsters performing account takeovers. There are many ways to infect a user, some being an email compromise or others planting malware that provides remote access to a computer. More niche services include targeted leads where they go after high-value businesses or bank employees. These leads will require special handling, and usually, another human is involved in trying to understand the scenario to exploit.
As seen above, a fraudster is advertising these typical services as a one-stop shop for bank fraud. A lot of technology goes behind these setups, and the more advanced ones have automated them to scale fake messages sent to thousands of people. They also utilize Email and SMS flooders, which will try to hide alerts and notifications about a wire. This is similar to the behavior we detailed about fraudsters performing account takeovers. There are many ways to infect a user, some being an email compromise or others planting malware that provides remote access to a computer. More niche services include targeted leads where they go after high-value businesses or bank employees. These leads will require special handling, and usually, another human is involved in trying to understand the scenario to exploit.
They can do phishing pages that capture cookies and device information. If a bank sees a transfer from the same device and IP, they might assume the request is safe. However, hackers will send a fake .docx with a RAT (Remote access tool) that captures all logins or can use a VNC to control the PC at a later time. Malicious USBs (BadUSB) left in a company's lobby or cafeteria with the business logo are another way. Fraudsters even talk about wearing construction vests to bypass questioning and then putting the USB on a shutdown computer to infect it later when it is turned on.
Another message seen was from a scammer who was looking for help with their operations. Many of these people have specialties that require them to connect with other fraudsters to steal funds.
"NEED A TEAM TO INFECT PC WITH VIRUSES AND HVNC AND GET CRYPTO TARGETS PM IF YOU HAVE ANY KNOWLEDGE OR KNOW HOW TO ENCRYPT AND SPOOF THE VICTIM pm "- Fraudster
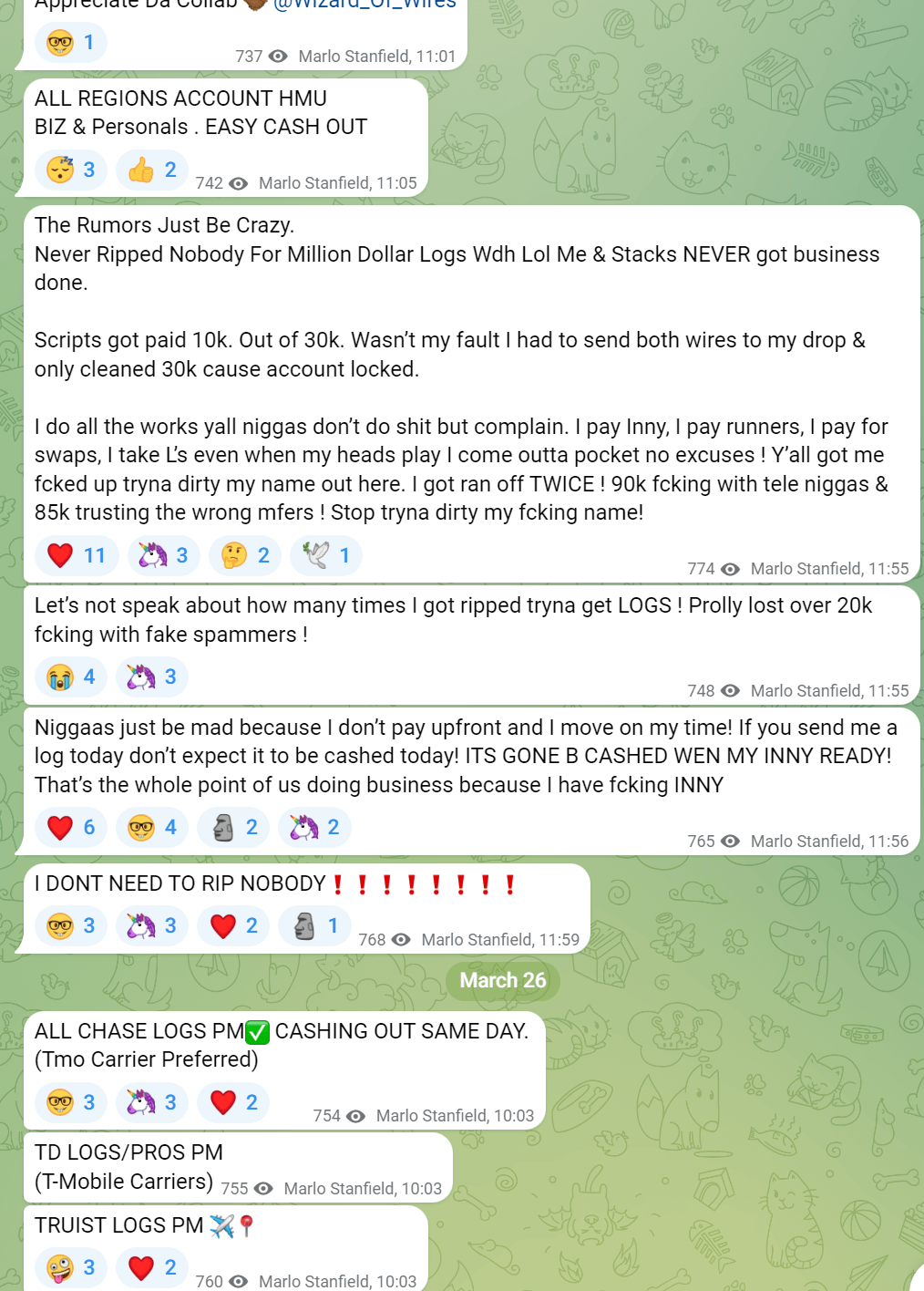
However, even the fraudsters get scammed by other fraudsters, so their trust in one another is difficult, limiting their knowledge sharing. The worst scenario is when fraudsters start sharing their intelligence with others, which then causes more scaling to this underground economy. For example, the teams that can do every step themselves make off with many stolen funds as they have the whole operation set up like a business. They will have a technology person with deep knowledge of wires and banks. Sometimes, they will have an inside person at a bank or branch who will knowingly allow the fraud to happen and appear negligent.
This is why it's critical to have certain checks and balances that can be audited with dual approvals and other monitoring. Unfortunately, there are currently few solutions for this type of software, but we have developed solutions that can aid in the process. Most of the solutions out there now are for real estate transactions only. Finboa, Caso, and FPSGOLD are examples of robust software that can integrate with a Core system but come with high costs and few authentication options compared to Trust Swiftly. Businesses familiar with tools like SailPoint, which has robust approval and certification workflows, can find some similar SaaS no-code workflow and approval options. The key is ensuring these tools are also highly secure, as the fraudsters will eventually try to break into them. Ensuring there is 2-factor authentication, SAML authentication, and compliance with SOC2 and other security standards is a must.
One workaround they have developed is through out-of-band bank wire requests that avoid online banking. They can initiate wires through email, a huge vulnerability that opens you up to BEC (business email compromise). Even if a fellow employee receives a request via email from another bank employee, do not trust it. The fraudsters can take over one key staff member's email and wait for the perfect opportunity to send a transfer request. They could also compromise the original customer's email so they have a chain of ownership that will make the transfer appear legitimate. Additional identity verification steps are critical to stop these threats if you still decide to allow them. A simple callback may not be enough in the future with SIM swaps in conjunction with AI voice cloning. Unfortunately, even knowing a voice may not thwart the fraudsters who had previously contacted your client to get a sample of their voice to create a custom voice model.
Other initiated wires, such as by phone call-ins, branches, or faxes, are also ripe for vulnerabilities. If you support these methods, be wary of large transfers and have a robust authentication process. Trust Swiftly has FIDO2 passwordless authentication for additional security that can stop OTP attacks. A massive issue in adding these other security controls is the lack of integration with existing core systems and the added costs of using the APIs from companies like Fiserv. A siloed process adds protections and can allow your bank to implement these security measures in weeks instead of months. Fraudsters even talk about SIM swaps, which can obtain the 2nd-factor authentication code. Knowing your customer and behavior is essential to notice any abnormal wires. For example, is your client suddenly doing a wire by phone when they have almost always done it in person? See the below chats between fraudsters talking about the economics of a wire fraud scam that involves a SIM swap.
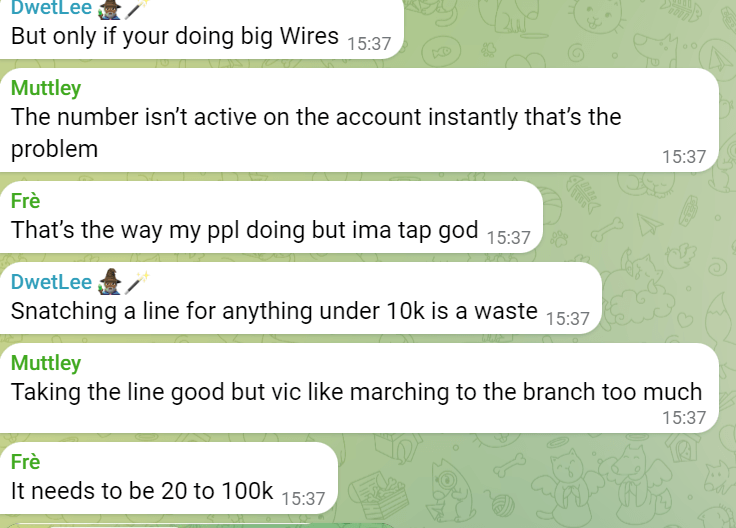
In these cases, callbacks may be insufficient unless your bank staff is very good at detecting fraud. Sometimes, these scammers hire professionals who prepare for the call, like a job interview, ensuring they know all the details and sound like the actual account owner.
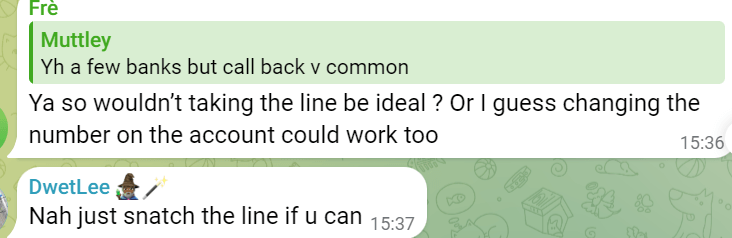
Furthermore, they can even wait until you are out of the country to do the compromise. Certain sellers have leads of targets, and then they monitor their phone via HLR to see the status of the person. There are specialists for each step of these scams, such as a researcher that finds a CEO or banker's personal email and information for lateral movements when attempting wire and bank fraud.
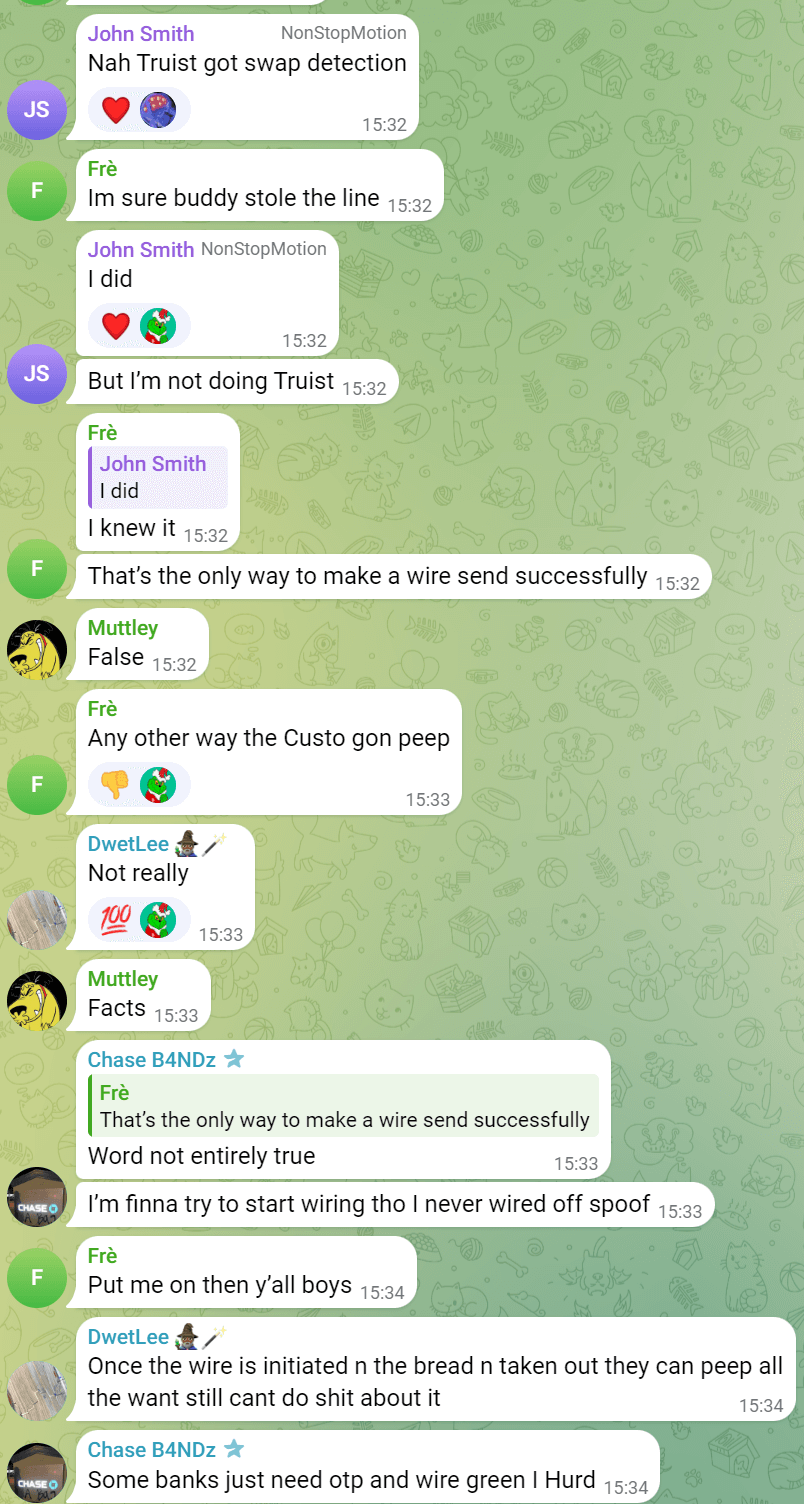
They go into as much depth to learn which security protocols you have in place and which banks are easier targets than others. For example, here they are talking about phone number swap detection by the bank Truist. A suitable prevention method should be checked for hire value transfers when the costs are minimal. Trust Swiftly can help with these types of checks and ensure you use appropriate active and passive detection systems. Another security protocol is the one-time passwords sent to a customer. In these cases, they do not even have to do an expensive line swap and trick your client into sending the code. The video below shows that they have automated bots to make the entire process easy for fraudsters. Your customer will receive a call from a spoof number, i.e., it could be your bank number, and then hear an alert about some fraud that needs a code to confirm themselves. In many cases, people will fall for this and reply with the code your banking application sent. They can do this to access an account or even add a digital credit/debit card to the hacker's phone.
Now that we have explored the entry points and ways that a fraudster might initiate a wire, they still have to cash out the funds. In the next part, we briefly explain some of their strategies. Again, being familiar with odd or international banks can save the hassle of sending funds to the wrong place. Checking the beneficiary or receiving bank can help you determine any details about the request. Also, requiring substantiating evidence for the wire, such as an invoice or real estate transaction offer, can help determine the legitimacy.

Cashing out is tricky, and they can sometimes employ 30+ people to access the funds. In this example, the person explains the documents needed to pull off the scheme. Having a way to validate IDs and information and seeing abnormalities in a transfer request can spot them before the funds are lost. Successive transfers in small amounts can be a way to go under the radar, and having a single large limit for extra security checks will not catch everything. Business bank logins are of higher value to these fraudsters because of their spare time to get the funds. Businesses sometimes won't notice a missing 20k wire immediately, while a single person is usually more aware of these fund transfers. That is why the timing of a wire is critical to understand: the fraudsters are waiting for the opportune time to extract the funds. The money then will go to different "runners" who withdraw the funds via ATMs as cash. They can also risk wiring the money internationally, which usually triggers other fraud alerts that freeze the funds. There are so many cash-out methods that we did not explore many, as that is another security tool that requires machine learning and AI to help detect.
As seen in this video, a person receives many cloned debit cards that they can use to withdraw funds whenever a wire is sent to a fraudulent account. Typically, one big wire is sent to a holding bank and then disbursed to other accounts so that the funds can be withdrawn to an untraceable or unfreezable method of money. i.e. cash, crypto, other accomplices.
In the end, this is just scratching the surface of the underlying banking fraud. Countless communities on the dark web and Telegram are all working to exploit bank controls. Having monitoring and authentication systems is one step that can stop fraudulent wires. Employee education is another factor that should be implemented, and having clients restrict wires is another option. Businesses especially need strong controls, secondary approvers for large wires, and easy ways to be alerted about a transfer. Notifying the originator's email and SMS is one option, but an automated call with information about the transfer is even better. Informing a client about a transfer can help prevent inside threats from BEC. Unfortunately, there is not one solution or software out there that can cover all the steps, so it takes multiple security tools to provide more protection. The attackers come from all sides, using hacking, phishing, social engineering, and more to achieve their goals. Especially hit are the banks that lack the technology to catch the fraud if they have processes disconnected from their core banking system. Keeping a personal touch with your clients is still possible, but there needs to be extra mitigating security to control the risk. Billions are lost yearly to ACH, debit, and wire fraud, so it's time to turn the tide with a new approach to your banking operations.